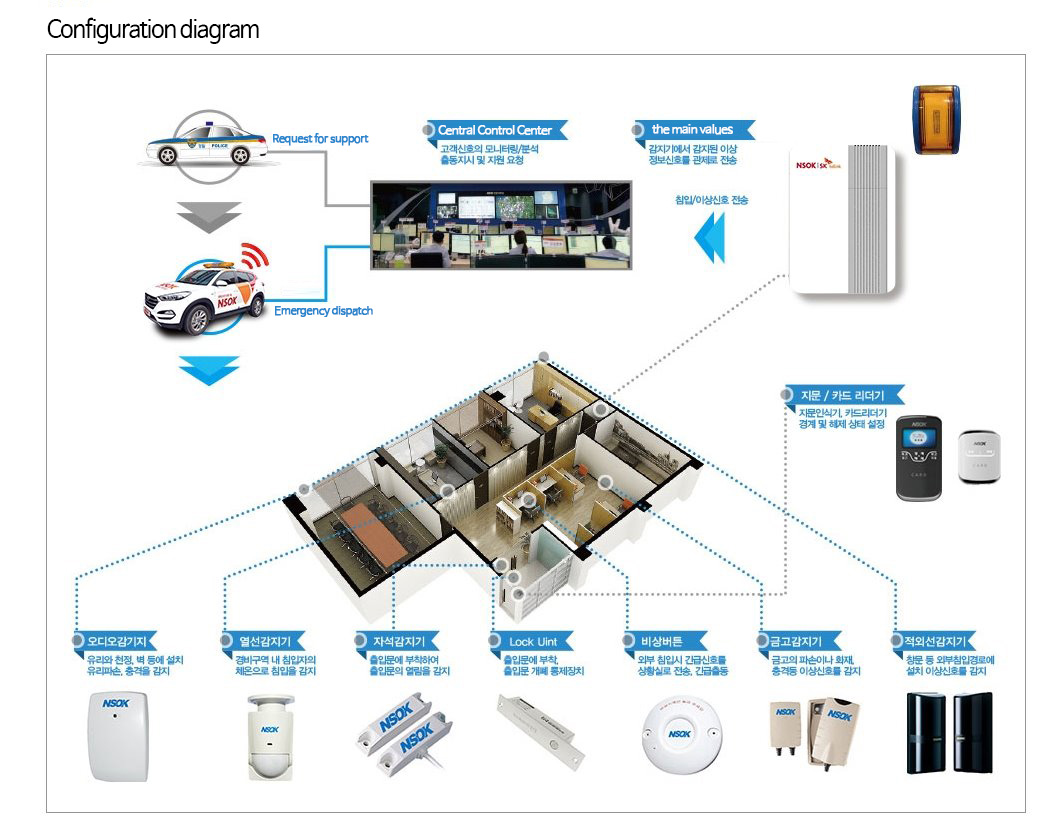
There are no clear regulations on how long CCTV information should be stored. It is only known that it is stored for about 30 days, whether in the public or private sector. In some cases, it is stored for longer than this, so individual confirmation is required.
Where CCTV is installed, a sign must be attached. The sign has the name and contact information of the person in charge of management. You can check the video by requesting the CCTV video information you filmed at the place where you manage the CCTV.

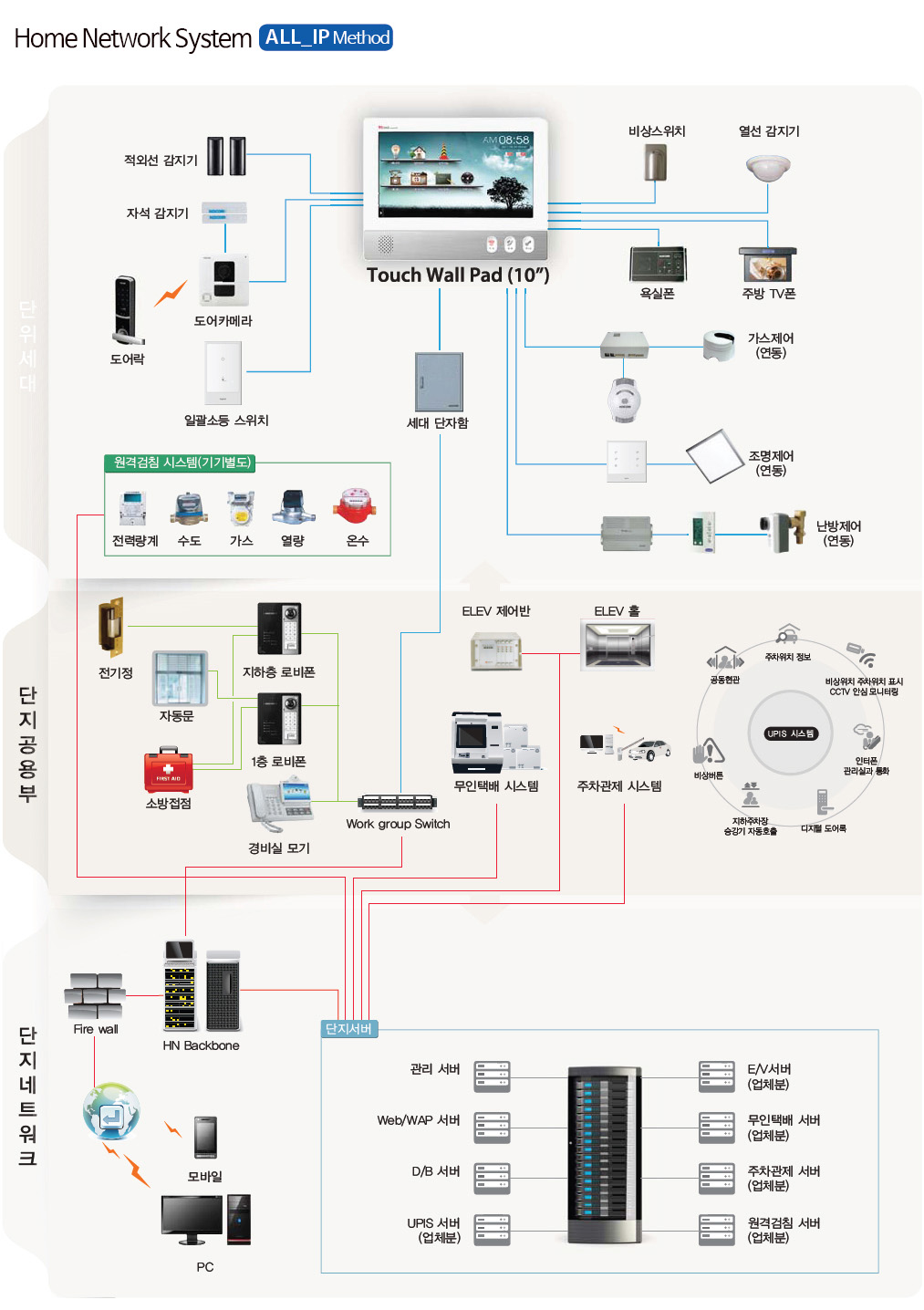
expectation effectiveness
- Camera installed at major locations inside and outside the building to monitor the images of passengers and traffic vehicles
- Prevention of accidents by users and emergency measures in the event of accidents
- Safety of users, employees, and facilities
- Dealing with destruction and theft of facilities by outside intruders
- High-function, low-employee efficient security management
- One person can control and monitor all systems
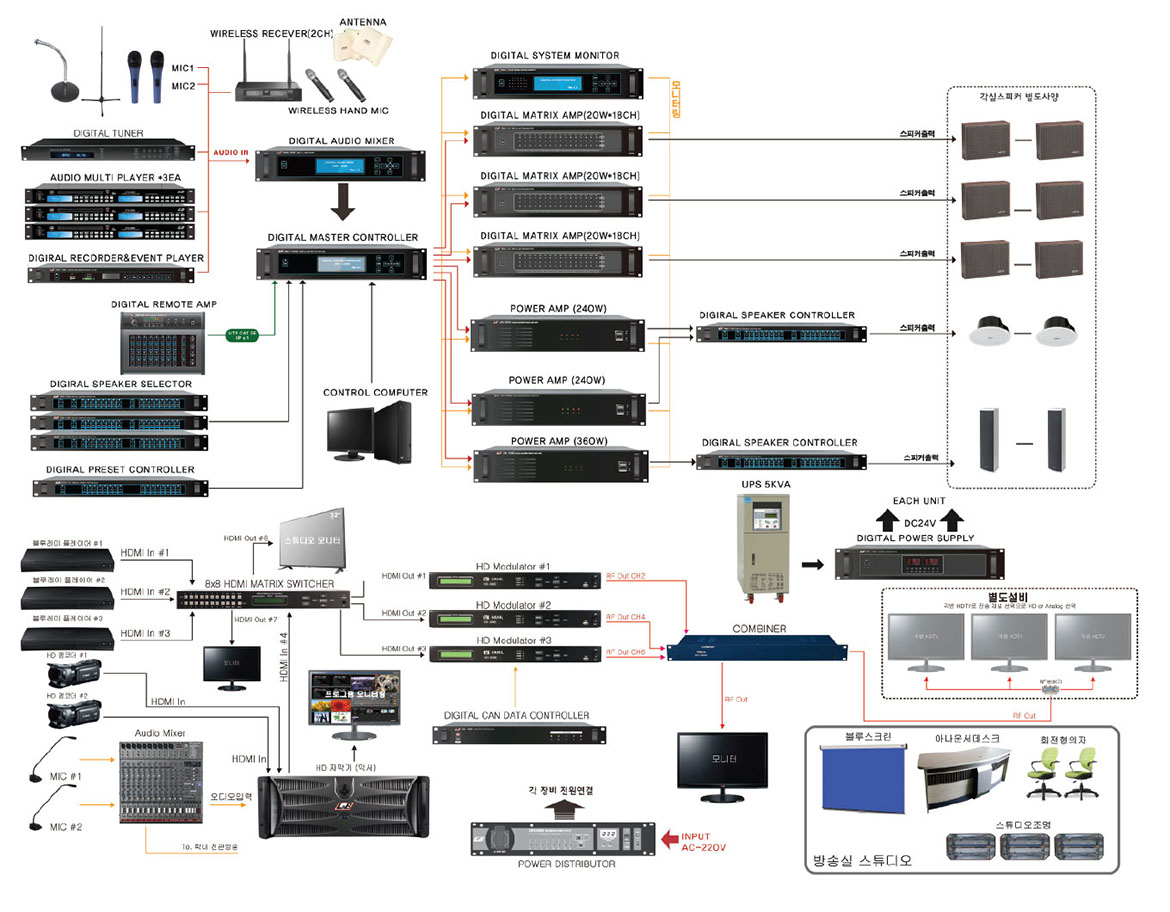
2. Broadcasting System
Large-scale broadcasting facilities RACK SYSTEM

Characteristics
1. It is easy to install in a large building.
2. It is possible to control all equipment with the PC program.
3. All equipment can be controlled anytime, anywhere via the Internet
4. Speakers can output any sound source from your PC
6. Automatic emergency broadcasting function
7. Broadcast history can be checked and outputted
Applications
All emergency broadcasting and general broadcasting are required, such as supermarkets, buildings, school government offices, public playgrounds, auditoriums, and training center church factories
It can be applied to the building and is intended to be used.
Medium-sized Broadcasting Facility RACK SYSTEM

Characteristics
1. It is easy to install in a medium-sized space.
2 Anyone can easily install broadcast equipment.
3. Built-in features such as DVD, CD, radio, Mixer, AMP, etc
4. External pressure function allows all voice equipment to be connected.
5. Built-in USB memory PLAY function
7. Built-in automatic emergency broadcasting is possible through linking P-type/R-type fire receivers.
8. Remote amplifier connection remote control
- Applicable fields: hypermarkets, convenience stores, shopping malls, golf courses, fitness centers, auditoriums, popular restaurants, gas stations, small conference rooms, lecture rooms
We offer meals in small places such as kindergartens, parking lots, village halls, and academies.
DIGITAL WATER BROADCASTING SYSTEM
Characteristics
- By applying the CAN 2.0 communication method as an equipment control communication method, errors were detected with a transmission speed of up to 1 Mbps and a CRC error code of 15 bits to prevent data loss due to retransmission requests in case of errors and secure the stability of the equipment at a transmission speed about 9 times faster than the existing RS communication method.
- By integrating and simplifying the system, cost reduction and stability are ensured – emergency broadcasting, clock signal function, remote amplifier control function, BGM control function, battery charging function, etc.
- The digital audio mixer is configured to enable eight-won broadcasting with 16 inputs and eight outputs, and all functions of the audio mixer and sound source equipment such as radios, CD players, and cassettes can be controlled by the Windows program.
- Network communication – It can be controlled and transmitted through the network, so that equipment can be controlled and broadcasted anywhere the network is configured.
- The time-voice function allows you to freely change the desired sound source using the MP3 sound source stored in SDCARD.
- It provides a security system, broadcasting in conjunction with fire broadcasting, and 16 preset functions to store and use preset values simply.
3.CATV
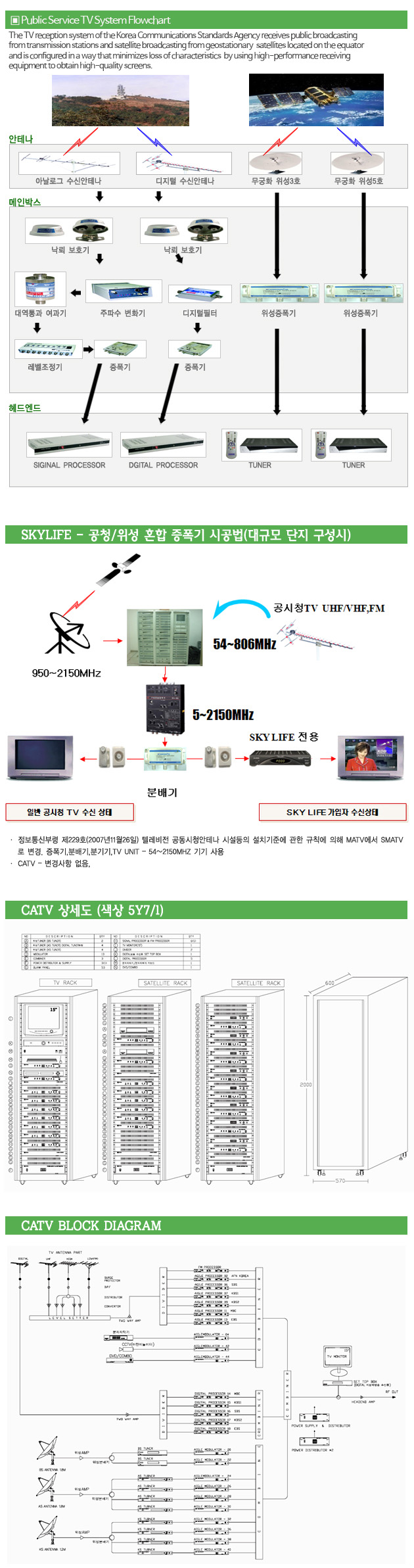
Public Service TV System Flowchart
The TV reception system of the Korea Communications Standards Agency receives public broadcasting from transmission stations and satellite broadcasting from geostationary satellites located on the equator, and configures it in a way that minimizes loss of characteristics by using high-performance inspection equipment to obtain high-quality screens.
Crypto Analysis Transaction Visualization (CATV) is the name of the most recently released security solution product on the Sentinel Protocol. Once a hot topic for businesses and organizations in recent years, cybersecurity issues have now emerged as a daily issue for all Internet users. I would like to introduce six important features of the Crypto Analysis Transaction Visualization tool among the many features it has.
1. Automatic mapping of cryptocurrency transactions: After signing up for the Sentinel portal, CATV will become available, allowing users to automatically map the transaction flow of a particular wallet address through a simple search. Distribution Department, Source Department, Transaction limit, and Date range are options that users can specify when tracking transaction history.
2. Fast transaction tracking: In the case of coin theft such as hacking, the flow of stolen funds can be provided in a visual graph without having to manually check the wallet and each transaction history, significantly reducing the response time related to anti-money laundering and terrorist funding.
3. Providing the latest crowdsourcing-based security threat information in real time: The basis of all Sentinel Protocol products, including new CATV tools, is the Threat Reputation Database (TRDB). Users will be provided with the latest crowdsourcing-based security threat information that is updated in real time.
4. Decentralization and non-reversibility guarantees: By storing TRDB in a blockchain, the non-reversibility of data is guaranteed. Through this storage method, threat information is not only disclosed to all others, but also a single point of failure (Single Point Of Failure) disappears.
5. Anti-money laundering and anti-terrorism financing: CATV tools can help prevent criminals from monetizing stolen cryptocurrency assets through money laundering when used by law enforcement and related agencies such as cryptocurrency exchanges
6. Automatically generating transaction history reports: One of the specialized features of the CATV tool, it is possible to automatically generate related reports based on the entire transaction history list corresponding to the visualized graph.
And these characteristics allow users to experience a new level of security services. There are two main ways to benefit from using CATV tools.
Indirect Benefits: Companies, organizations, and crypto exchanges using CATV tools can ensure that end users have their digital assets protected in a safer ecosystem.
Direct Benefits: Users can try the CATV tool for free by accessing the following link. https://portal.sentinelprotocol.io/signup (Free trial for 1000 first-come, first-served people) Registered users can all search for the wallet address they want, track the funds with one click and automatically check the summarized transaction flow. This allows users to track how much remittance transactions started at the wallet address they entered have progressed, and at the same time track the inflow path of funds to that wallet address.
Follow Uppsala Security forum and Sentinel Protocol's SNS accounts on Twitter, Telegram, LinkedIn and Facebook for the latest news.
4. Information and communication business
Integrated Wiring System
Overview
- Infrastructure for organically and integrated connection of integrated wiring management functions
- Scalability and affordability of services to respond to environmental changes
- Possessing information communication and information processing functions
- Integrate into functions and structures that correspond to buildings and all communication facilities
Components of SYSTEM